
Fingerprinting disguised HTTP servers
 |
Fingerprinting disguised HTTP servers |
The following report shows httprint detecting the underlying web server of sites using disguised web servers.
Comparing with Netcraft's web server survey, we find httprint's results to be consistent with the underlying operating system and the web server hosted on it.
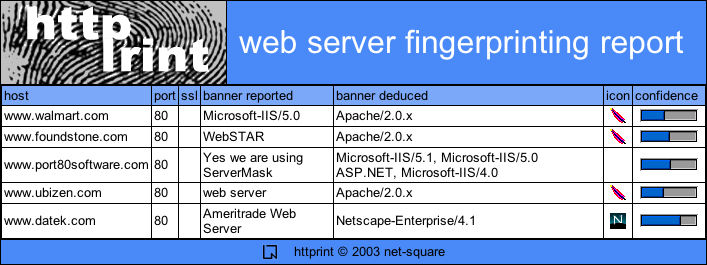
Tracing through the server banner history, it can be seen that the underlying operating system is always a Unix server. Along the way sometimes the Apache server banner has been observed. At other times, a "Microsoft-IIS/1.3.26" banner has been observed, which indicates an improper obfuscation attempt. The underlying server is indeed Apache.
In this case, the underlying operating system has always been OpenBSD/NetBSD. The server banner string started out as Apache, and then subsequently, it was changed to Netscape-Enterprise, and then to WebSTAR. In one of the entries, an improper obfuscation attempt displays the Apache extended server banner string "(Unix) mod_ssl/2.8.6 OpenSSL/0.9.6c". This confirms the underlying server is Apache.
Port 80 software makes a product called ServerMask, which modifies the HTTP headers to make the responses appear to be those of another server. They seem to be running IIS on Windows, along with their product (which is only for IIS). It can be seen how the server string keeps changing, yet the underlying operating system has been consistently detected as Windows. The underlying server is Microsoft-IIS.
Ubizen's HTTP server response returns a banner string of "web server". httprint detects the web server as Apache, which is consistent with the underlying operating systems reported by Netcraft.
Datek's web server is actually a Netscape Enterprise server, but displaying the customised banner string as "Ameritrade Web Server". httprint infers the underlying web server accurately as Netscape-Enterprise.
|
|