Max Vision, http://maxvision.net/
OVERVIEW
This morning, January 2nd 2000, I witnessed an attempted takeover of one of my domains, MAXVISION.NET. The attacker, calling themself "Mnemonic of the group KeyRoot", using an AOL.COM address, attempted to spoof a request from me to change the primary and secondary DNS servers for my domain, to Network Solutions / Internic. If successful, this request would effectively give them control of maxvision.net until I could have sorted it out with my place of registration. The attempt at hijacking the domain was foiled for several reasons, which I will outline below.
THE ATTACK
The attacker sent a forged Domain Modification form to Internic. There were several incompotent errors in the submission that caused the submission to fail. Had these errors not been made, and had I relied on the MAIL-FROM mechanism of Internic, then control of my domain would have been effectively hijacked.
Overview of forged email path:
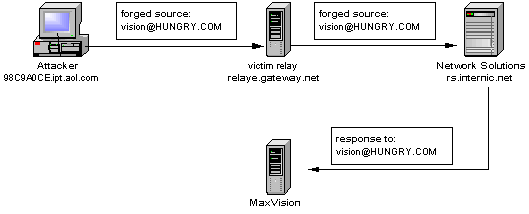
The first sign that something was going on was an email from Internic, confirming "my request".
| Email confirmation "response" from Internic |
| Date:
Sun, 2 Jan 2000 17:19:50 -0500 (EST)
From: hostmaster@internic.net To: Max Vision <vision@HUNGRY.COM> Subject: Re: [NIC-000102.b318] Re: MODIFY DOMAIN maxvision.net This
is an automatic reply from Network Solutions to acknowledge that
If
you need to correspond with us regarding this request, please be
Regards,
|
| Email error "response" from Internic |
| Date:
Sun, 2 Jan 2000 17:20:29 -0500 (EST)
From: Domain Registration Role Account <domreg@internic.net> Reply-To: hostmaster@internic.net To: vision@HUNGRY.COM Subject: Re: [NIC-000102.b318] MAXVISION.NET The
Domain Name Registration Agreement below has been returned to you due
The
glossary of the parser errors is available at
Network
Solutions Registration Services
dreg08 The
attacker had tried to use the same DNS server as primary and secondary
Either
the hostname or the IP address of a name server matches that of
The
From header was spoofed, the upper case indicates it was copied from my
whois record
|
The trail of evidence is overwhelming. Here is the breakdown, then I'll discuss each element:
- attacker, using an AOL.COM IP address, send forged email using GATEWAY.NET mail relay. This is known to be true, since the networksolutions.com mail server (rs.internic.net) is resistant to TCP spoofing, as is relaye.gateway.net.
- the AOL.COM address was inactive, so they must have disconnected immediately after sending the forged email (AOL absolutely does not care *at all* about this, and all attempts to reach the abuse or security teams of AOL, Gateway.NET, and Internic have yielded no reply. NO WONDER.)
- the contact information was all false. The only point of control that the attacker gets is the DNS service.
- If the attacker intended Denial of Service, then they might not have control of the Linux DNS server.
- If the attacker intended control of the domain, then they either own/operate the Linux DNS server, or they have rooted the machine.
-
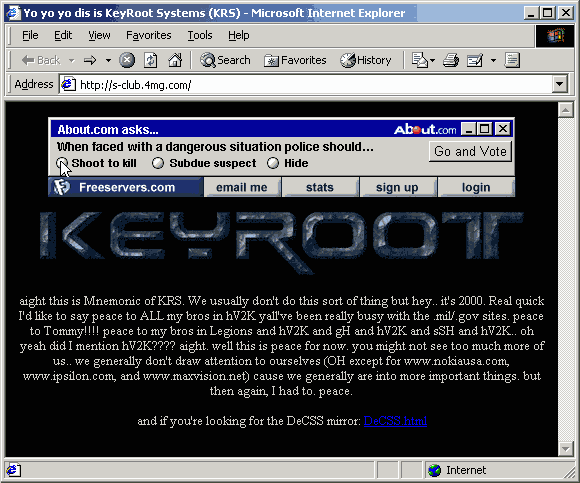
The Linux
DNS server is a freeservers.com webhosting server - when the HTTP/1.1 hostname
s-club.4mg.com is used, the following webpage appears (indicating that they do have control of the linux server, and that they intended to hijack my domain and Nokia's):
Internic's
mail server is not vulnerable to TCP spoofing, which indicates that the
header information is valid - that a mail really did reach their servers
from the relay host, relaye.gateway.net. [Update: note that this machine
is not a Linux box, for those curious about the possibility of other spoofing
methods not involving sequence number prediction]
| not spoofed: rs.internic.net |
| rs.internic.net
(198.41.0.6)
TCP
Sequence Prediction:
|
relaye.gateway.net
is also not vulnerable to TCP spoofing, which indicates that the header
information is valid - that a mail really did reach their servers from
the attacker, 98C9A0CE.ipt.aol.com [152.201.160.206].
| not spoofed: mail relay host |
| relaye.gateway.net
(208.230.117.253):
TCP
Sequence Prediction:
|
Based on this information, the liklihood of the email being truly forged (at the packet level) are extremely low. This appears to be a straightforward application-level forgery from the AOL account.
Having
a look at the DNS server that the attacker was trying to substitute for
mine, to control the domain, we see it is an older Linux system, that is
acting as a virtual webserver. I have contacted that rightful administrators
of the system about the attempted attack.
| overview: substitute dns server |
| FreeServers.com
- www26 Server Provo, Utah - USA
www26.freeservers.com (209.210.67.126): Port State Protocol Service 21 open tcp ftp 23 open tcp telnet 25 open tcp smtp 37 open tcp time 80 open tcp http 111 open tcp sunrpc 113 open tcp auth 513 open tcp login 514 open tcp shell 2049 open tcp nfs 3306 open tcp mysql TCP
Sequence Prediction:
|
HOW TO DEFEND YOURSELF
Internic
offers three authentication methods for domain administrators. MAIL-FROM,
CRYPT-PW, and PGP. Each can be used to effectively protect against this
type of hijacking effect, each with increasing levels of effectiveness.
The following are summaries that discuss how each is used. After each description
I'll briefly discuss their vulnerabilities.
| MAIL-FROM |
| MAIL-FROM
is the most basic type of authentication scheme. Under this level of protection,
Network Solutions will verify that a Domain Name Registration Agreement,
Contact Form or Host Form was submitted from the e-mail address, as listed
in our database, of the administrative or technical contact of the record
to be changed.
MAIL-FROM checks to see that requests to update your contact record -- or any record that you are associated with -- are sent from the current E-mail address of the contact. By default, all the contacts in the database have MAIL-FROM protection unless they have used the Contact Form to associate their contact record with a PGP key or an encrypted password. MAIL-FROM is the default authentication scheme. If you are not sure which of the three options to select, choose MAIL-FROM - it is the default. |
MAIL-FROM
is the default, and weakest security level. Don't follow their advice,
use CRYPT-PW at the minimum.
| CRYPT-PW |
| In
the protection hierarchy, encrypted password, or CRYPT-PW, is the next
highest level of protection for a domain name registration record. CRYPT-PW
allows updates to be submitted from any e-mail address, and, if the correct
password is supplied, Network Solutions will process the Domain Name Registration
Agreement, Contact Form or Host Form.
If
you would like to guard your contact record -- and any other database records
that you are a contact for -- with a password, enter the plain text of
the password in the box below. After you enter the password in the box
below it will be encrypted and entered on the form in the correct place.
Enter the password a second time to verify that you have entered the plain
text of the password correctly.
|
CRYPT-PW
is a more secure authentication mechanism, as it requires the use of the
correct password to effect a domain change. This may be exceedingly difficult
to guess, as Internic may have anti-password-guessing measures in place
to curb endless "guesses".
| PGP *NetSol may have stopped supporting PGP* |
| Pretty
Good Privacy provides the highest level of security. PGP is an encryption
and digital signature scheme. While 100% security can never be guaranteed,
PGP is a very safe scheme. In order to use PGP as your authentication scheme,
the PGP software must be installed on your computer. This software is available
both commercially and as freeware.
If you wish to protect your contact record -- and all records that you are a listed contact for -- with Pretty Good Privacy encryption software, choose this option. IMPORTANT: You must obtain the PGP software and install it on your computer before you can use this security feature. PGP is available commercially and as shareware. To find out more about getting started with PGP, read our help files on how to obtain and install PGP. Your PGP key MUST be added to the Network Solutions' key server before you can use the Contact Form to associate a PGP public key with this contact. Enter the key ID of your PGP public key in the box below. If you have installed the PGP software on your machine but you do not know your key ID, type: pgp -kvc on your local machine to discover the eight digit key ID of your PGP key. IMPORTANT: If you have selected PGP, keep in mind that when the contact template is generated and E-mailed to you, you must FIRST sign the update request with your secret PGP key before sending the contact template to NetworkSsolutions. |
PGP is the strongest security level, as it is virtually impossible for an attacker to guess the correct private key. PGP is widely held to be one of the more secure/trusted forms of encryption/authentication.
There
are also settings for "Notification Levels" for updates or usage. If an
attacker is aware of this, they can forge the request email, and then forge
an additional ACK email.
| Notification Levels |
| The
administrative and technical contact/agent will each choose when they would
like to be notified to validate a Domain Name Registration Agreement, Contact
Form or Host Form. The options they can choose from are: BEFORE-UPDATE;
AFTER-UPDATE; and NOT-CARE. The administrative and technical contacts are
not required to choose the same option. Network Solutions will act upon
the first reply we receive.
If the contact selects BEFORE-UPDATE, Network Solutions will send a confirmation request before any changes are made, even if the request was received from an authorized source. The contact then has the opportunity to acknowledge the validity of the request by replying "ACK" or "YES" to the notification. If the contact does not agree with the change request, replying "NAK" or "NO" to the notification will prevent any changes from being made. Selecting BEFORE-UPDATE may delay legitimate changes while Network Solutions waits for approval to make the requested change. If the contact selects AFTER-UPDATE, Network Solutions will send a confirmation request after changes have been made. Even if AFTER-UPDATE is the selected level of protection, Network Solutions will only process a Domain Name Registration Agreement, Contact Form or Host Form if it was received from an authorized source, or if the registrant gives its express written permission to make the requested change. Both the administrative and technical contacts have the opportunity to acknowledge the validity of the request by replying "ACK" or "YES" to the notification. If either one of the contacts does not agree with the change request, replying "NAK" or "NO" to the notification will usually reverse any changes that were made. AFTER-UPDATE is the default option if no other type of notification is selected. If the contact selects NOT-CARE, Network Solutions will never send a confirmation to that contact. By choosing this option, the contact establishes that they are not concerned about whether or not authorized changes are made to any domain name registration, contact record or host record with which he is associated. |
As
stated above, MAIL-FROM is not really enhanced with the BEFORE-UPDATE feature,
as an attacker could forge a corresponding ACK message.
CONCLUSION
There are some serious security issues with the current Internic Guardian system. Domain Hijacking is as easy as ever, and many newbie crackers have been actively using this attack to hijack websites addresses. Over the Y2K weekend it was rumored that several large sites suffered from this attack. If you are a domain contact and have not set encryption authentication options such as CRYPT-PW or PGP, then DO SO NOW!
Max
Vision
http://whitehats.com/
http://maxvision.net/