|
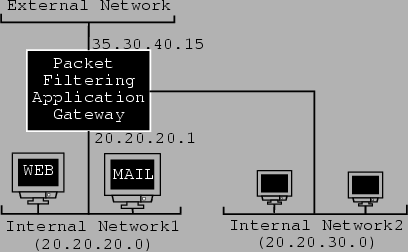
Figure 8.1 shows a network diagram with a firewall implemented as a packet filter between the internal and external networks. In figure 8.2, a new internal network is introduced, separated from the main network or backbone by a router. Figure 8.3 represents a combined solution to the problem of network security, combining both packet filtering and application proxying.
This view of the world is more secure than any one of the firewalling methods by itself. The design philosophy is that there are levels in the security or firewall organization. Figure 8.4 shows this hierarchical design of the authentication method.
Consider inbound traffic coming into the firewall host. Since our packet filtering is built into the kernel, it happens first. This is our first defence mechanism. If the packet gets through our packet filtering process, it is passed on to the next level. The next level may be application proxying or a connection to the destination host. Let us consider what happens when the packet has to go through an application gateway. The source address will be checked for permission to the service. If that matches, depending on whether authentication is required for the service, user authentication for the service is required. We can see that we therefore have three levels of defense instead of one in the case of a packet host or two for the application gateway. Outgoing traffic goes through the same process.
It should be clear that the most secure option with the combined solution is for every packet to go through all three types of available authentication and authorization. This could be implemented by rejecting everything at the packet filtering level except that which is authenticated by a later application gateway. For a service such as telnet, with this model, a packet filter can be less strict on the premise that whatever gets through it will be 'caught' by the application gateway. A more secure configuration might restrict telnet on source address both on the packet filter and the application gateway. If by some chance an unauthorized packet gets through the packet filter, it will be denied access to the service by the application gateway.
TIS FWTK and ipfwadm have been tested and are known to co-exist merrily. All that is needed to convert an existing configuration of either the packet filter or the application gateway is to install the component of the combined firewall solution that is missing. Access lists need then be modified to allow access only to services provided for by the application gateway.