|
The TIS FWTK is a suite consisting of the following components:
The suite includes proxy servers for telnet, ftp, SMTP, rlogin and http. A plug-board connection server is also provided. The plug-board server is included primarily for use in proxying Network News. It can be used as a proxy for other services for which custom proxy servers do not exist. The proxy servers generally replace the normal service daemons. However, the normal service daemons can be configured for use together with the gateways. We will see an example of how to achieve this in the example section. For an in-depth look at proxy server setup together with their perfomance issues, the reader is referred to [16].
All the proxy servers are configurable and indeed are configured from a central file, called ``netperm-table''. This file contains information on the configuration of each service, including any restricted access information.
Access lists to services are provided by a program called ``netacl''. Through this program, are run all the services that require restricted access. As mentioned above, all the proxies are configured in a central file. It is this same file that is used by the ``netacl'' program in its evaluation of who is allowed to use which service. Network access control is based on the source IP address. In this sense, it plays a similar purpose to a packet filter, but at a higher level.
The authentication server provides a second level of restriction for services. This is the layer of the application gateway that discriminates by username and password pairs. The authentication server allows new users and groups to be created in the authentication server database. User and group administrators can add new users and give privileges to other users. The authentication server is provided mainly for the rlogin and telnet services. Although it can be used with other services, it is designed for, and works for, the aforementioned services.
The only client programs supplied with the version of the firewall that we obtained are ftp and telnet clients. Both these clients allow the user to be completely unaware of the firewall. When users use the above-mentioned clients, they only have to worry about their destination host. Connections to the firewall, and the connections from the firewall to the destination host, are handled by the clients. If authentication is required for the service on the firewall, the user is prompted for the relevant information.
As mentioned in our initial discussion of application proxies, they log more, and better than packet filters. Since they work at the service level and not only with source and destination addresses and ports, they log all the relevant information about a connection to a service. The reporting scripts allow for easy reporting on the information that has been logged. They parse the log files and report on the service whose statistics are required, the day's statistics or the week's statistics.
The toolkit comes with extensive documentation. The documentation can be separated into four categories:
The toolkit is distributed with a version of the syslog daemon. A sample configuration of this new daemon is included as part of the kit. A local configuration file on how to start the services when the host ``boots up'' is also included. Examples of how to run the services from the inetd daemon are also included. Finally, a sample ``netperm-table'' is included to show how to provide and restrict access to the proxies.
An entry in the ``/etc/inetd.conf'' file for telnet looks may follows :
netacl-in.telnetd: permit-hosts * -exec /usr/local/etc/tn-gw
The next keyword of interest in the above rules is ``permit-''. Entries beginning with ``permit-'' or ``deny-'' are flagged internally as either granting or revoking permission to the service. The next keyword is ``hosts''. This keyword gives us the ability to list the names and/or IP addresses of hosts we wish to allow to use the service. Wildcards are allowed as arguments for this keyword. The next keyword to note is ``-exec''. This allows us to execute different programs depending on where the request to the service originated. The keyword is followed by the complete path of the program to be executed.
The above rules allow hosts on the network 146.231.128.x to telnet into the firewall machine and be able to login into the firewall itself. All other hosts that telnet into the firewall machine are presented with the telnet gateway. Rules for the telnet gateway would have to be specified in the netperm-table file if it is being executed.
The netacl program provides access control for programs that have been invoked by inetd. Instead of inetd calling the service itself, it calls netacl. Netacl then searches through the rules in the netperm-table file for ones that matches the requested service. If the host that initiated the connection is found to have authorization to access the service, the real server is run. If the host is found not to have authorization, the request is logged and netacl exits.
Netacl comes with a few options but we shall only consider a few. The first option is the ``hosts'' option. This option is the same keyword that we identified above when looking at an example of a service configuration. It allows us to list the hosts which are allowed or denied (flagged by permit- or deny-) to use a certain service. The list of hosts allowed or denied access to a service is optionally followed by a options flags. ``-exec'', we have already shown above, is one of these options. The other option we will consider is the ``-user'' option. It allows us to specify who the server is run as. An example of a command including all the options follows:
The telnet gateway also comes with a variety options. As with the netacl program, we shall consider only the few which are of particular interest to us. Configuration lines for the telnet gateway and for all the other proxies appear in the netperm-table file as follows:
tn-gw: welcome-msg /usr/local/etc/telnet-welcome.txt
tn-gw: denydest-msg /usr/local/etc/telnet-denydest.txt
The FTP gateway provides in the same manner as discussed for the telnet gateway, the rules ``denial-msg'', ``welcome-msg'' and ``denydest-msg''. The gateway also provides a ``hosts'' rule. The options that may be applied to this rule differ from the telnet gateway's and will be discussed. The first option to note is the ``-log''. The option specifies the operations to log. It takes either the form ``-log operation'' or ``-log {operation1 operation2 ...}''. The next option to note is the ``-auth'' option. This option specifies commands which may not be executed except when authenticated. It takes either the form ``-auth operation'' or ``-auth {operation1 operation2 ...}''. The last option for our consideration is the ``-dest'' option. This functions in the same way as in the telnet gateway. A sample follows:
-log { retr stor } -dest !*.com
smapd has five configuration rules that we will consider. The first of the configuration rules is mandatory and is the ``executable''. The parameter to this rule is the path to the smapd executable. The next rule we shall consider is ``sendmail''. Its parameter specifies the path to the sendmail or other mail transfer agent (MTA). The ``userid'' rule's parameter specifies the userid under which smapd is to be run, for security reasons. The ``directory'' rule has its parameter specifying the spool directory. It should be noted that this spool directory has to be readable and writable by the userid given with the ``userid'' option. The last of the smapd rules is ``wakeup''. This specifies the amount of time (in seconds) after which smapd should check the spool directory for new mail.
smap also has ``userid'' and ``directory'' rules. These rules can be shared with the smapd rules. The next rule to consider is the ``maxbytes'' rule. It specifies the maximum amount of bytes that a mail message is allowed to be. The last of our smap rules for consideration is the ``timeout'' rule which specifies the amount of time (in seconds) smap should wait when collecting a message before giving up on it.
Example rules for smapd and smap follow:
smap: maxbytes 4000
smapd: wakeup 60
smapd: executable /usr/local/etc/smapd
smapd: sendmail /usr/local/exim/bin/exim
smap, smapd: userid 511
smap, smapd: directory /var/spool/smap
The plug-board has two primary options. The ``timeout'' option works in the same way as the one described for SMTP gateway above. The second primary option is the ``port'' option. The ``port'' option is followed by the port-ID which may either be a port number or the name of a service associated with a port, from /etc/services. The port-ID represents the port to bind to. The port-ID is followed by a host-pattern which indicates hosts allowed to connect to that service. There are secondary options to the ``port'' option. The first is the ``-plug-to'' option. Its form is ``-plug-to hostname'' where hostname represents the host to connect requests on the port-ID to. The last secondary option we will discuss is the ``-port'' option. It's form is ``-port port-ID''. The port-ID in this case represents the host to connect to on the host specified by the ``-plug-to'' option. An example rule follows.
We will consider four of the five configuration rules the authentication server provides. The first rule under consideration is the ``database'' rule. This specifies the location of the authentication database. The database is stored in dbm(3) format. The second rule for consideration is the ``nobogus true'' rule. The rule specifies that the authentication server should be as unfriendly to the user as possible, returning ``Permission Denied'' instead of a useful error message. The third rule for noting is the ``badsleep'' rule. The rule specifies the number of seconds for which a user should be locked out after repeated bad logins. After more than five attempts when the ``badsleep'' value is not set, the user is locked out of the account. If the value is set however, the user may attempt to login after the number of seconds specified by the ``badsleep'' rule has expired. The last rule for our consideration is the ``hosts'' rule. The syntax and semantics of this rule are the same as for the previously discussed proxy servers. The difference with the ``hosts'' rule here is that if an optional DES key is supplied, communication will be encrypted and decrypted using the key. Sample authentication server configuration rules follow.
authsrv: permit-hosts 146.231.128.*
authsrv: nobogus true
authsrv: badsleep 1200
adduser siviwe 'Siviwe Kwatsha'
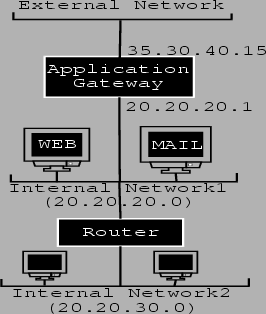
Our policy has the following requirements:
Our inetd(8) will start the required services using the ``netacl'' program. As we run both proxied and normal versions of the telnet and ftp services, we have a choice on how to run them. We can either decide to start the normal version of the services on a different port from the proxied one or run them both on the same port and use ``netacl''. We illustrate how to run both versions of the telnet service on the same port using ``netacl''. The proxied and normal FTP services will be run on different ports. Our ``/etc/inetd.conf'' file looks as follows:
1: ftp stream tcp nowait root /usr/local/etc/netacl in.ftpd
2: ftp2 stream tcp nowait root /usr/sbin/tcpd in.ftpd -l -a
3: telnet stream tcp nowait root /usr/local/etc/netacl in.telnetd
4: authsrv stream tcp nowait root /usr/local/etc/authsrv authsrv
% End of inetd.conf
The services we do not want to start from the inetd, can be started from this file. The only services which we require that have not been started from the inetd file are the SMTP services. From the example configuration of the ``rc.local'' file, we extract the following
% Start the SMTP queuer (smapd)
(cd /var/spool/mqueue; rm -f nf* lf*)
echo " smtp queuer"
/usr/local/etc/smapd &
% Script to deliver undelivered mail
/usr/local/etc/mqueue &
% Start the SMTP listener (actual mail daemon that binds to port 25)
echo " smtp listener"
/usr/local/etc/smap -daemon &
It should be noted that all the services could be started from the rc.local file. The inetd handles the starting and termination of services for us and is therefore the preferred method of starting some services. Starting them ourselves from the rc.local file, while they will work the same way, means that if the process we start (the parent) dies, we no longer provide that service. With inetd, connections to the port always succeed if the daemon can be found and inetd itself is running. An example how to start the services from the rc.local file through netacl follows
netacl-in.telnetd: permit-hosts 20.20.20.* -exec /usr/sbin/in.telnetd
netacl-in.telnetd: permit-hosts * -exec /usr/local/etc/tn-gw
% FTP access
netacl-in.ftpd: permit-hosts * -exec /usr/local/etc/ftp-gw
% Telnet gateway
tn-gw: denial-msg /usr/local/etc/telnet-deny.txt
tn-gw: welcome-msg /usr/local/etc/telnet-welcome.txt
tn-gw: denydest-msg /usr/local/etc/telnet-denydest.txt
tn-gw: hosts 20.20.30.* -dest !*.hack.com -dest !firewall -auth
tn-gw: hosts * -dest !firewall -auth
% Ftp Gateway
ftp-gw: denial-msg /usr/local/etc/ftp-deny.txt
ftp-gw: welcome-msg /usr/local/etc/ftp-welcome.txt
ftp-gw: denydest-msg /usr/local/etc/ftp-denydest.txt
ftp-gw: deny-hosts 20.20.30.*
ftp-gw: permit-hosts * -auth { nlist } -dest !firewall -log { retr stor }
% Smap and Smapd
smap, smapd: userid 511
smap, smapd: directory /var/spool/smap
smapd: executable /usr/local/etc/smapd
smapd: sendmail /usr/local/exim/bin/exim
smap: maxbytes 4000
smap: timeout 3600
% Authentication server
authsrv: database /usr/local/etc/database
authsrv: nobogus true
authsrv: badsleep 300
authsrv: hosts 20.20.*
% Clients that can use authentication server
*: authserver 127.0.0.1 5544